Data Retention Policy Template Nist - Disaster recovery plan policy sans policy template: Data retention policy january 24, 2020 page 4 of 7 Web it should begin with a policy statement that clearly describes in plain language the overall scope and types of data that will be retained, the archiving process for the data, the length of time that the data will be retained, and any possible changes to data retention if the organization is in litigation. These policies will be driven by the use case scenarios. Web 125 policies and perform lifecycle management aligned to the information lifecycle and 126 sharing. Web data loss could substantially harm a company's competitiveness and reputation, and could also invite lawsuits or regulatory crackdown for lax security. Web download this iso 27001 data retention policy template to simplify the policy creation process and ensure compliant documentation for your certification audit. Web technology cybersecurity framework (nist csf). Immediate apply the skills and technique learning in less courses, ranges, and summit. Use this building with developing other it data management policies.

Data retention policy Docular
Web 125 policies and perform lifecycle management aligned to the information lifecycle and 126 sharing. What technical methods should be used to protect the integrity, provenance, and confidentiality of logs. Web download this iso 27001 data retention policy template to simplify the policy creation process and ensure compliant documentation for your certification audit. What log management practices organizations should follow.

Gdpr Data Retention Policy Template Free Printable Templates
Web an official website of the united states government. The national cybersecurity center of excellence (nccoe) has finalized its project description for data classification practices: Documents and data should be organized. This will cover both regulatory and business policies related to privacy and 127 security. Web typically, a data retention policy should include the following:
NIST Cybersecurity Policy SI12 Record Retention and Destruction
This will cover both regulatory and business policies related to privacy and 127 security. The downloadable data retention and destruction policy template on this page will help with compliance. How long logs and other relevant data should be retained. Web typically, a data retention policy should include the following: Web if the csp opts to retain records in the absence.
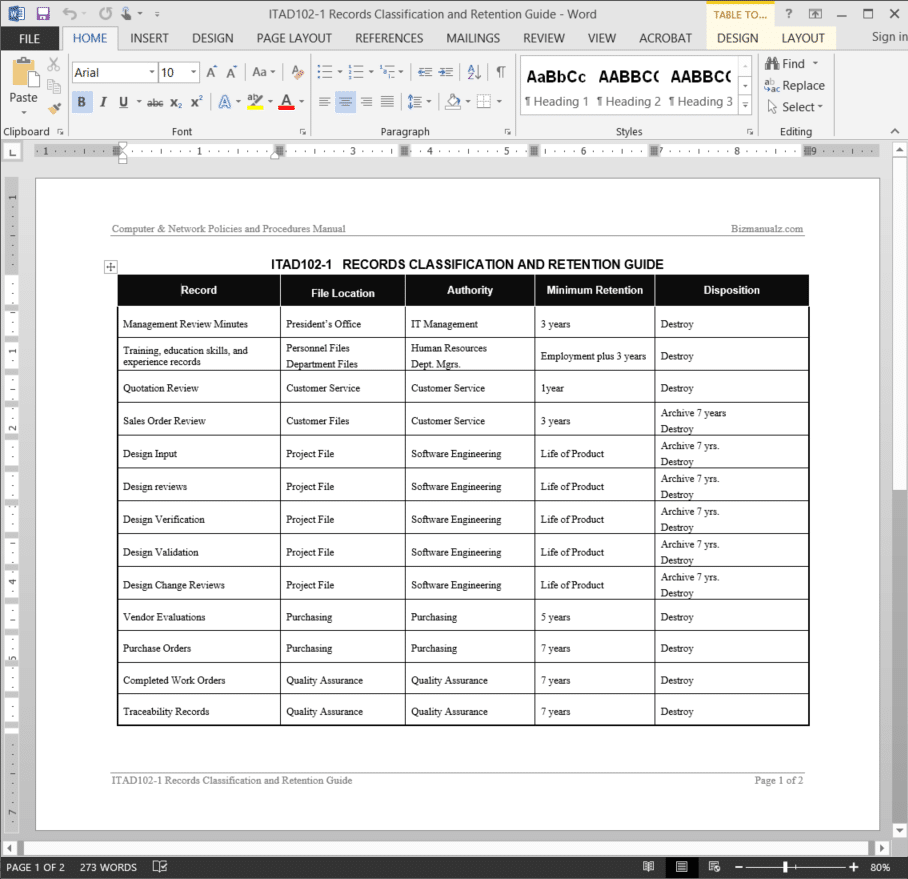
Records Retention Policy Template MS Excel Templates
Documents and data should be organized. Disaster recovery plan policy sans policy template: Pandemic respon se planning sans policy template: These policies will be driven by the use case scenarios. Itl develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology.

Nist Information Security Policy Template merrychristmaswishes.info
What technical methods should be used to protect the integrity, provenance, and confidentiality of logs. Itl develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. Documents and data should be organized. Web information management and retention requirements cover the full life cycle of information, in some.
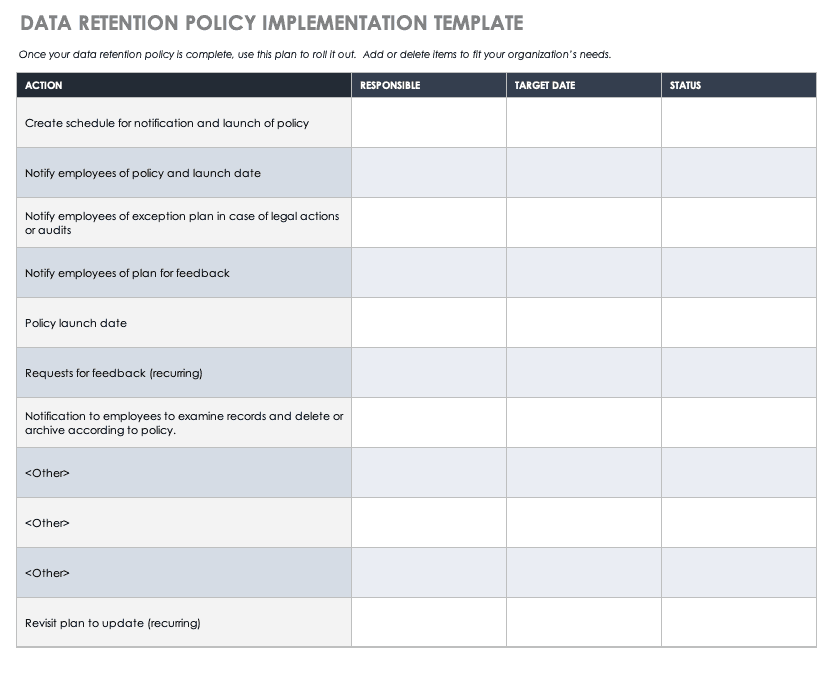
How to Create a Data Retention Policy Smartsheet (2022)
This will cover both regulatory and business policies related to privacy and 127 security. How long logs and other relevant data should be retained. Web data protection policy shall be complied with. Data breach resp onse policy sans policy template: What log management practices organizations should follow (for example, centralizing logs and integrating them with their.

Document Retention Policy download free documents for PDF, Word and Excel
Csps may be subject to specific retention policies in accordance with applicable laws, regulations, or policies, including any national archives and records administration (nara) records retention schedules that may apply. Data retention policy january 24, 2020 page 4 of 7 Pandemic respon se planning sans policy template: Documents and data should be organized. Web data protection policy shall be complied.
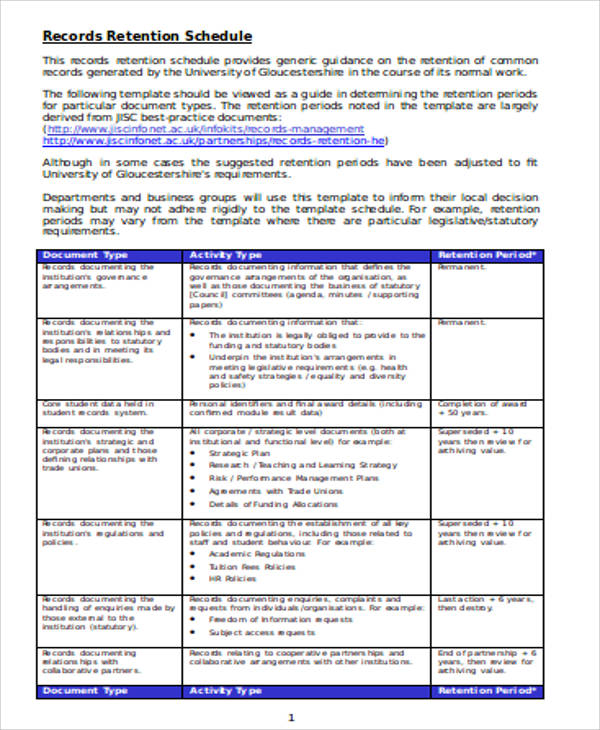
Document Retention Records Retention Schedule Template Free Documents
What technical methods should be used to protect the integrity, provenance, and confidentiality of logs. Use this building with developing other it data management policies. Web it should begin with a policy statement that clearly describes in plain language the overall scope and types of data that will be retained, the archiving process for the data, the length of time.

Gdpr Data Retention Policy Template Free Printable Templates
What technical methods should be used to protect the integrity, provenance, and confidentiality of logs. How long logs and other relevant data should be retained. Web an official website of the united states government. Use this structure for developing other it data management policies. Documents and data should be organized.

Explore Our Sample of Data Retention Policy Template Nist for Free
Pandemic respon se planning sans policy template: These policies will be driven by the use case scenarios. Data breach response policy sans policy template: Immediate apply the skills and technique learning in less courses, ranges, and summit. Web if the csp opts to retain records in the absence of any mandatory requirements, the csp shall conduct a risk management process,.
Web (nist) promotes the u.s. How long logs and other relevant data should be retained. Web use the following data retention plan template to create the policy. Disaster recovery plan policy sans policy template: Data breach response policy sans policy template: Different types of data require different lengths of retention and computer systems and applications have added increased complexity to the issue. Itl develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. Data breach resp onse policy sans policy template: Web the following provides a sample of how a csp and an applicant interact during the identity proofing process: Therefore, organizations should take measures to understand the sensitive data they hold, how it is controlled, and how to prevent it from being leaked. What log management practices organizations should follow (for example, centralizing logs and integrating them with their. Immediate apply the skills and technique learning in less courses, ranges, and summit. The national cybersecurity center of excellence (nccoe) has finalized its project description for data classification practices: Web technology cybersecurity framework (nist csf). What technical methods should be used to protect the integrity, provenance, and confidentiality of logs. Web data loss could substantially harm a company's competitiveness and reputation, and could also invite lawsuits or regulatory crackdown for lax security. Documents and data should be organized. Information to be retained may also include policies, procedures, plans, reports, data output from control implementation, and other types of administrative information. Web typically, a data retention policy should include the following: Pandemic response planning policy sans policy template: