Nist 800 30 Template - Nspue2 certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. 3.3.5, 3.6.1, 3.6.2, 3.6.3, 3.13.14. Cswp 3 (06/03/2014) author (s) joint task force abstract this publication describes the risk management framework (rmf) and provides guidelines for applying the rmf to information systems and organizations. Defense and aerospace organizations, federal organizations, and contractors, etc.) The preparer should determine what information is appropriate to • name, title, agency, address, email address, and phone number of person who owns the system. • unique identifier and name given to the system. Web the security response plan mentioned earlier is appropriate evidence for several controls: These templates include extensive comments and guidance about how to present the results a risk assessment in a way that can be understood. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an.
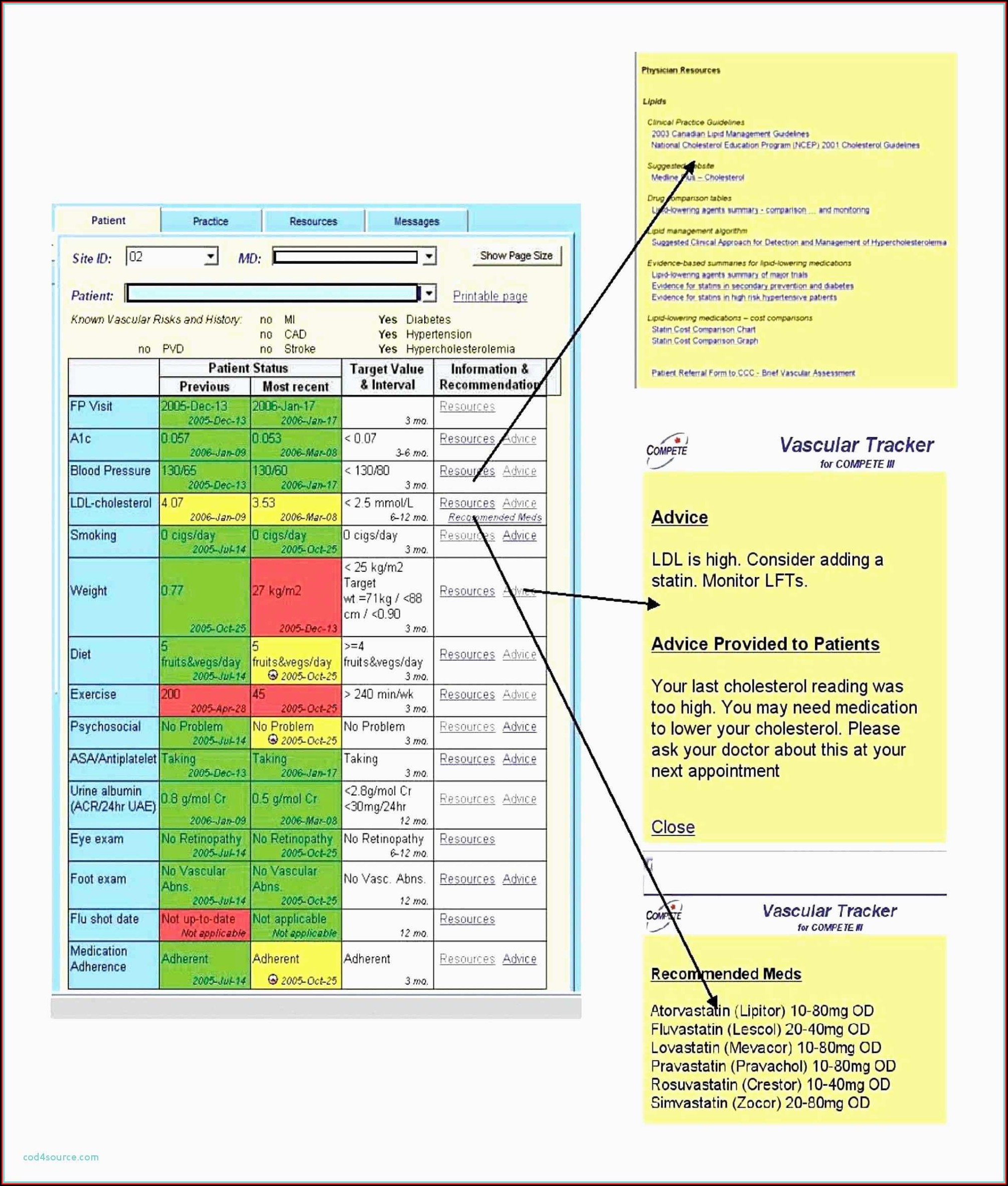
800 30 Risk Assessment Spreadsheet / Nist 800 53 Rev 4 Spreadsheet
The preparer should determine what information is appropriate to Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. 887 • reformatted all content to follow the latest nist technical publication template..

Professional Nist 800 30 Risk Assessment Template Doc Kelitbanganwonogiri
These templates include extensive comments and guidance about how to present the results a risk assessment in a way that can be understood. The preparer should adapt the format as needed. Vulnerability & patch management program. 887 • reformatted all content to follow the latest nist technical publication template. Web the federal government relies heavily on external service providers and.

Nist 800 Risk Assessment Template File Nist Sp 800 30 Figure 3 1 Png
Web the federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. These templates include extensive comments and guidance about how to present the results a risk assessment in a way that can be understood. Vulnerability & patch management program. Risk assessments, carried out at all three tiers in.

PPT NIST 80030 PowerPoint Presentation, free download ID3223960
• name, title, agency, address, email address, and phone number of person who owns the system. • identify the appropriate fips 199 categorization. Defense and aerospace organizations, federal organizations, and contractors, etc.) This document provides guidance for carrying out each of the three steps in the risk assessment process (i.e., prepare for the. An organization can use the.

Nist 800 Risk Assessment Template / of the national
The subjective aspects of writing a risk assessment report can be tricky to navigate. Web this publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets, individuals, other organizations, and the nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign.
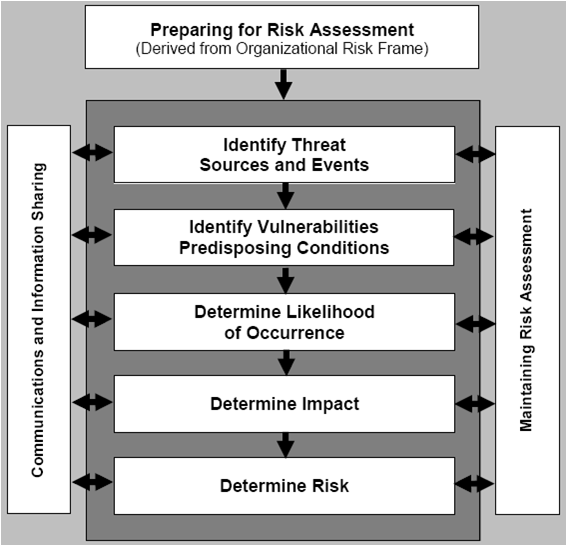
NIST SP80030 Risk Assessment Framework Risk Assessment Security
Vulnerability & patch management program. Web framing establishing the context for how organizations manage information assessment identify threat sources & events, vulnerabilities, determine risk (impact & security risk risk response develop risk response strategy (accept, reject, mitigate, share/transfer risk) & courses of action likelihood) & uncertainty monitoring Risk assessments, carried out at all three tiers in the risk management hierarchy,.
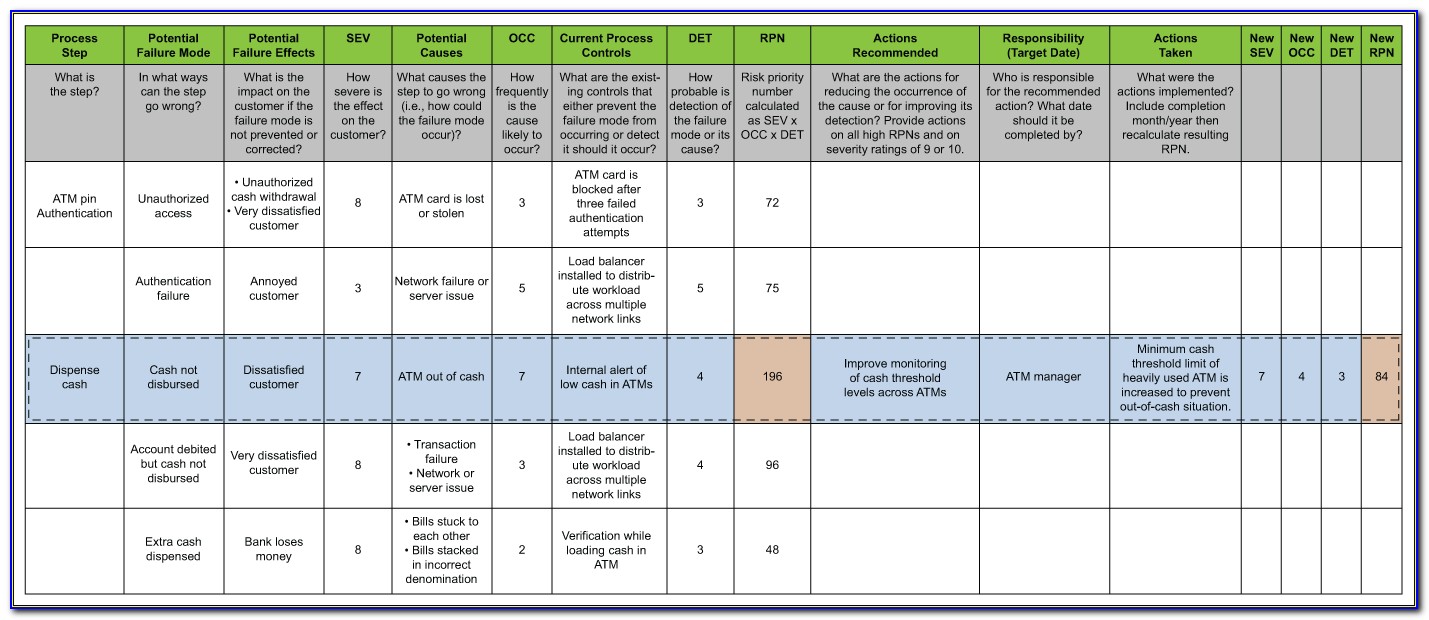
Nist 800 Risk Assessment Template / Nist 800 171 Template shatterlion
Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an. • unique identifier and name given to the system. Nspue2 certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Cswp 3 (06/03/2014) author (s) joint task force abstract this publication.

Editable Nist 800 30 Risk Assessment Template Word Sample
Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process. 887 • reformatted all content to follow the latest nist technical publication template. The subjective aspects of writing a risk assessment report can be tricky to navigate. This standard provides a template for preparing an rar in support of.
Nist 800 Risk Assessment Template NIST 80030 Risk Assessment. by
• unique identifier and name given to the system. Web this publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets, individuals, other organizations, and the nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign intellig. • name, title, agency,.
Nist 800 Risk Assessment Template File Nist Sp 800 30 Figure 3 1 Png
Web framing establishing the context for how organizations manage information assessment identify threat sources & events, vulnerabilities, determine risk (impact & security risk risk response develop risk response strategy (accept, reject, mitigate, share/transfer risk) & courses of action likelihood) & uncertainty monitoring • unique identifier and name given to the system. • name, title, agency, address, email address, and phone.
Vulnerability & patch management program. • identify the appropriate fips 199 categorization. Computer security division, information technology laboratory. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process. The preparer should determine what information is appropriate to Nspue2 certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an. These templates include extensive comments and guidance about how to present the results a risk assessment in a way that can be understood. This standard provides a template for preparing an rar in support of the rmf process as it applies to dhs nss. How to cite this nist technical series publication: 3.3.5, 3.6.1, 3.6.2, 3.6.3, 3.13.14. • name, title, agency, address, email address, and phone number of person who owns the system. An organization can use the. • unique identifier and name given to the system. Web this publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets, individuals, other organizations, and the nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign intellig. Web nist privacy risk assessment methodology (pram) the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. Web framing establishing the context for how organizations manage information assessment identify threat sources & events, vulnerabilities, determine risk (impact & security risk risk response develop risk response strategy (accept, reject, mitigate, share/transfer risk) & courses of action likelihood) & uncertainty monitoring Web the security response plan mentioned earlier is appropriate evidence for several controls: This document provides guidance for carrying out each of the three steps in the risk assessment process (i.e., prepare for the. The preparer should adapt the format as needed.