Nist 800 53 Ssp Template - Web abstract the objective of system security planning is to improve protection of information system resources. Includes new template and formatting changes. This includes publishing the nist technical series: Web record the sensitivity level for confidentiality, integrity and availability as high, moderate, or low. The protection of a system must be documented in a system security plan. Revised controls for language consistency and updated attachment 3</p> Web security and privacy control collaboration index template (excel & word) the collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that risks are appropriately managed. National institute of standards and. Security and privacy controls for information systems and organizations. The oscal ssp model enables full modeling of highly granular ssp content, including points of contact, system characteristics, and control satisfaction.

Nist 800 53 Rev 5 Controls Spreadsheet —
Security and privacy controls for information systems and organizations. 4 (12/18/2014) planning note (03/30/2022): Add more rows as needed to add more information types. The protection of a system must be documented in a system security plan. April 2013 (updated 1/22/2015) supersedes:

(4) NIST SP 80053 Revision 4 (security control enhancements omitted)…
Includes new template and formatting changes. This includes publishing the nist technical series: This publication is available free of charge from: 4 withdrawn on september 23, 2021. Web the oscal system security plan (ssp) model represents a description of the control implementation of an information system.
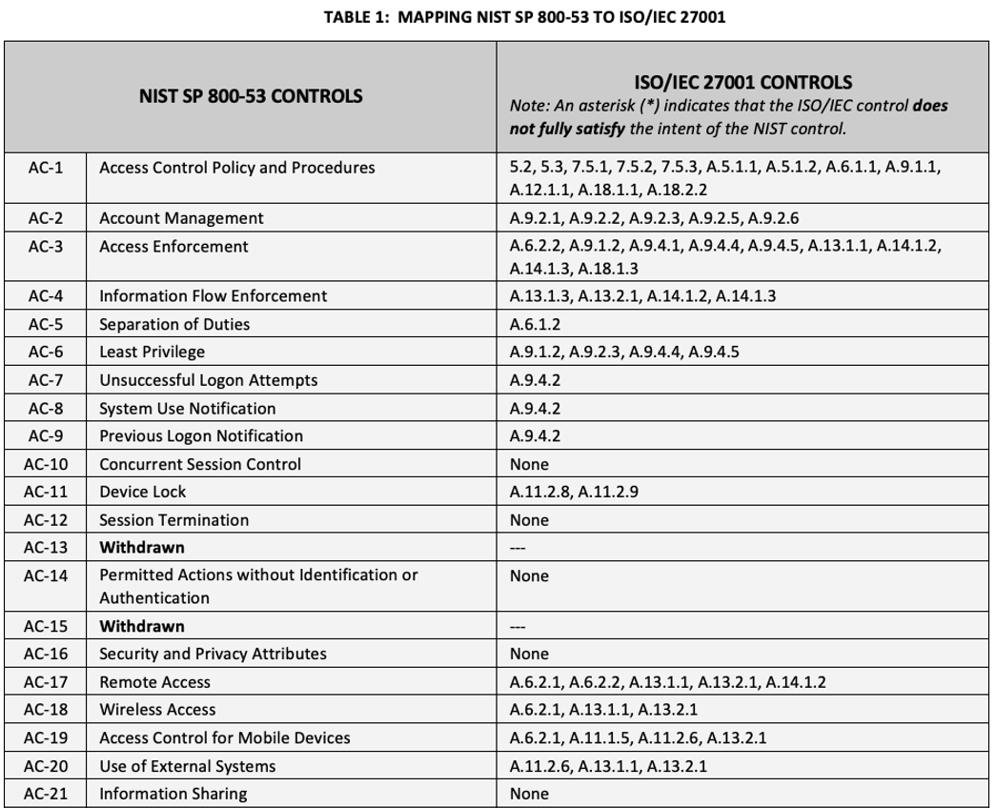
NIST 80053 Privileged Access Management, Security and Privacy
Revised controls for language consistency and updated attachment 3</p> The protection of a system must be documented in a system security plan. 5 assessing security and privacy controls in information systems and organizations date published: Includes new template and formatting changes. All federal systems have some level of sensitivity and require protection as part of good management practice.
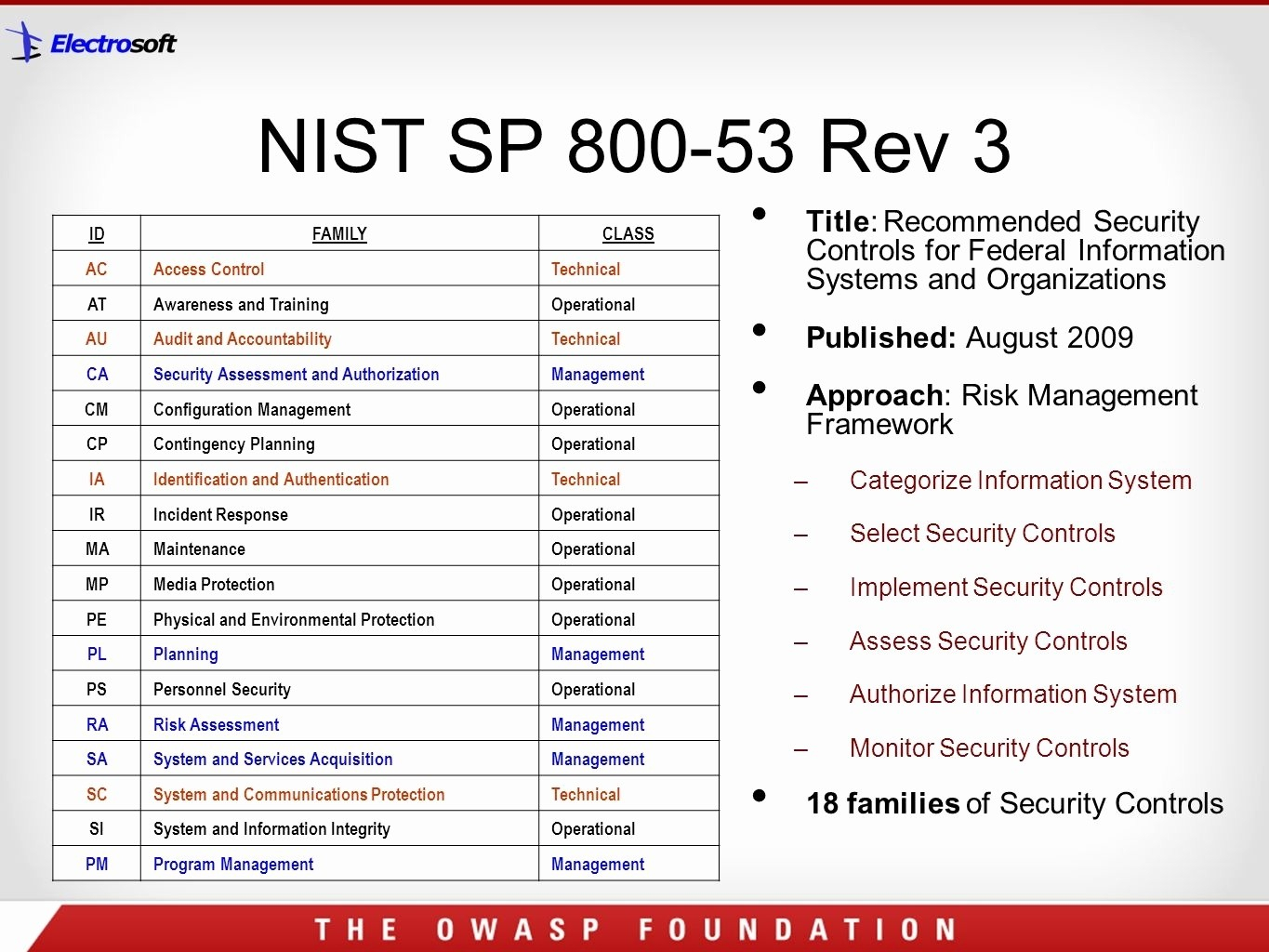
Nist Sp 800 53 Rev 4 Spreadsheet —
The ssp model is part of the oscal implementation layer. Revised controls for language consistency and updated attachment 3</p> April 2013 (updated 1/22/2015) supersedes: 5 security and privacy controls for federal information systems and organizations date published: Includes new template and formatting changes.
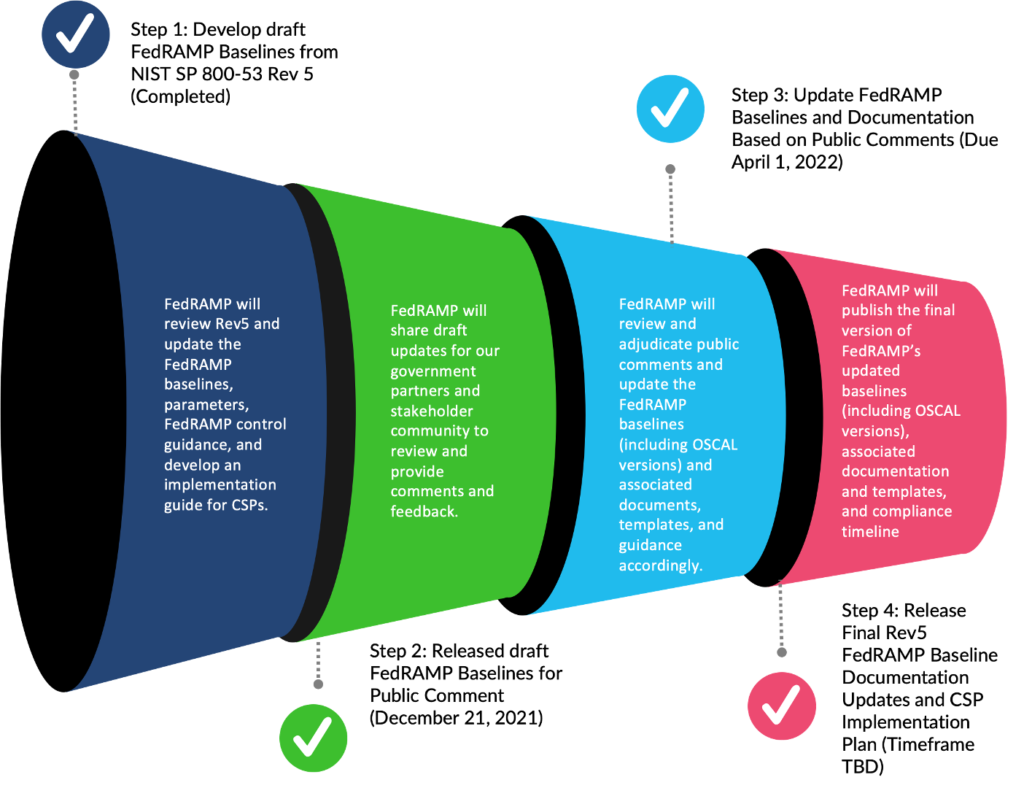
Planning for FedRAMP’s NIST SP 80053 Rev 5 Baseline
5 security and privacy controls for federal information systems and organizations date published: April 2013 (updated 1/22/2015) supersedes: Revised controls for language consistency and updated attachment 3</p> Web abstract the objective of system security planning is to improve protection of information system resources. Technical reports and journal of research of nist.

NIST 80053 Security Controls Lifeline Data Centers
Simply put, if you run support or “supply chain” operation, the defense federal acquisition regulation supplement (dfars) made specific cybersecurity protocols a requirement. Release draft fedramp baselines for public comment The ssp model is part of the oscal implementation layer. Web details resource identifier: This publication is available free of charge from:
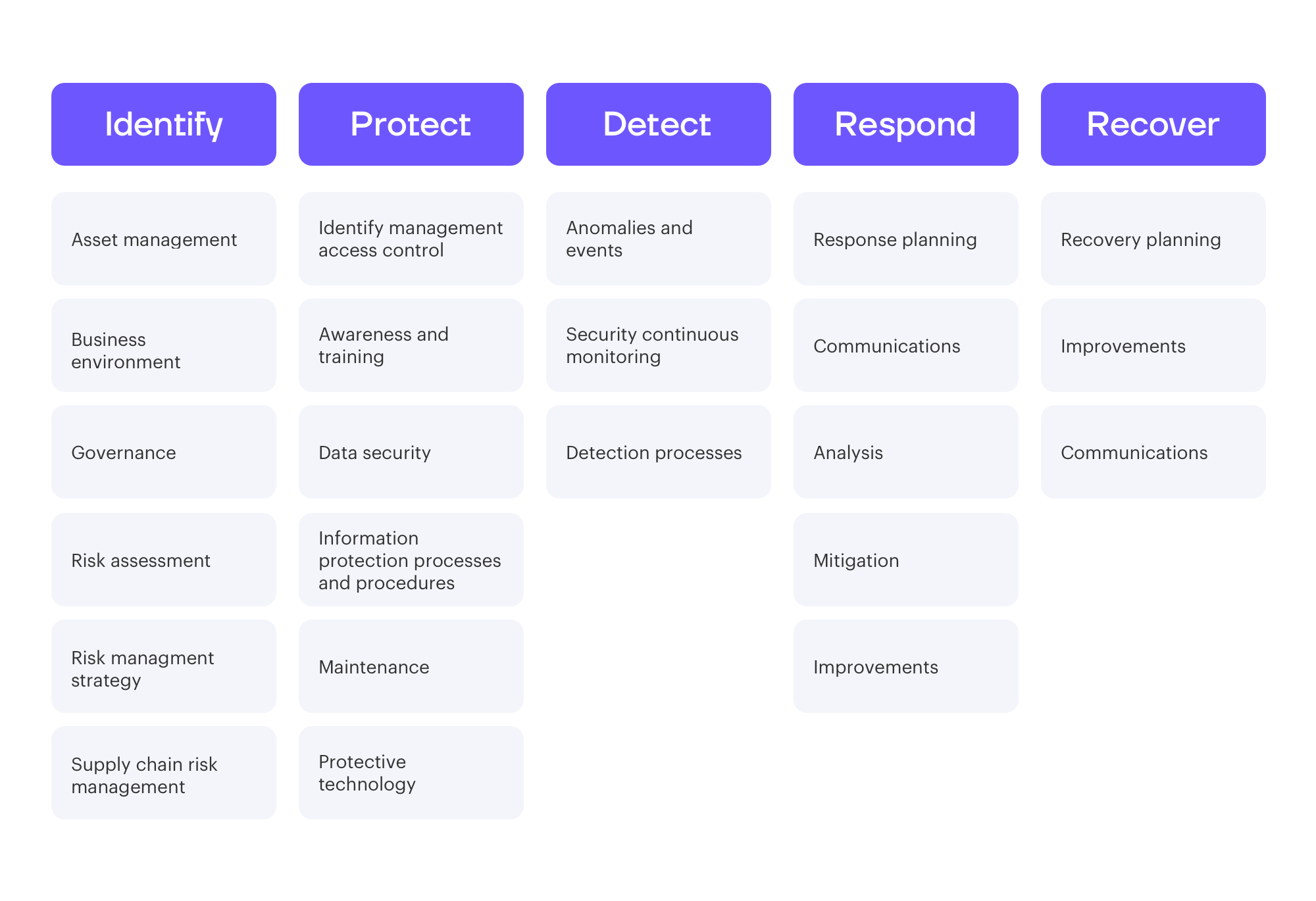
NIST 80053 rev. 5 compliance Qush blog
Web record the sensitivity level for confidentiality, integrity and availability as high, moderate, or low. Web details resource identifier: The oscal ssp model enables full modeling of highly granular ssp content, including points of contact, system characteristics, and control satisfaction. 5 assessing security and privacy controls in information systems and organizations date published: The protection of a system must be.

Nist 800 53 Policy Templates
Web abstract the objective of system security planning is to improve protection of information system resources. All federal systems have some level of sensitivity and require protection as part of good management practice. National institute of standards and. The protection of a system must be documented in a system security plan. Web details resource identifier:
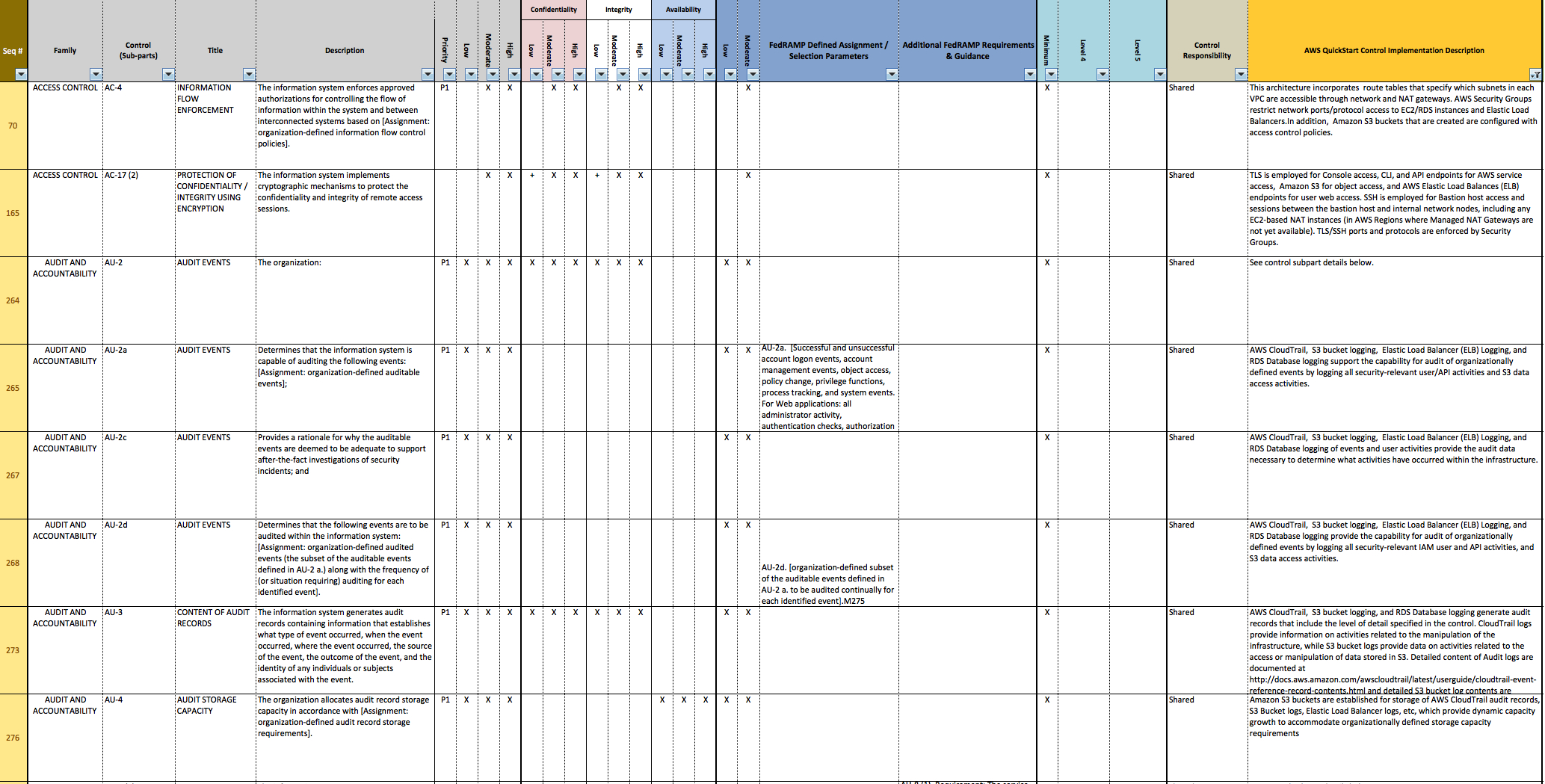
Nist 800 53 Security Controls Spreadsheet Google Spreadshee nist 80053
4 (12/18/2014) planning note (03/30/2022): This includes publishing the nist technical series: The protection of a system must be documented in a system security plan. Technical reports and journal of research of nist. Release draft fedramp baselines for public comment

NIST 800 53 Controls Flowchart
5 assessing security and privacy controls in information systems and organizations date published: Web cui ssp template ** there is no prescribed format or specified level of detail for system security plans. Technical reports and journal of research of nist. Web security and privacy control collaboration index template (excel & word) the collaboration index template supports information security and privacy.
Web the oscal system security plan (ssp) model represents a description of the control implementation of an information system. Web abstract the objective of system security planning is to improve protection of information system resources. Web record the sensitivity level for confidentiality, integrity and availability as high, moderate, or low. Includes new template and formatting changes. 5 security and privacy controls for federal information systems and organizations date published: Web cui ssp template ** there is no prescribed format or specified level of detail for system security plans. National institute of standards and. The protection of a system must be documented in a system security plan. 5 assessing security and privacy controls in information systems and organizations date published: 4 withdrawn on september 23, 2021. Add more rows as needed to add more information types. Web security and privacy control collaboration index template (excel & word) the collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that risks are appropriately managed. The oscal ssp model enables full modeling of highly granular ssp content, including points of contact, system characteristics, and control satisfaction. All federal systems have some level of sensitivity and require protection as part of good management practice. This publication is available free of charge from: Revised controls for language consistency and updated attachment 3</p> Technical reports and journal of research of nist. April 2013 (updated 1/22/2015) supersedes: Simply put, if you run support or “supply chain” operation, the defense federal acquisition regulation supplement (dfars) made specific cybersecurity protocols a requirement. The ssp model is part of the oscal implementation layer.